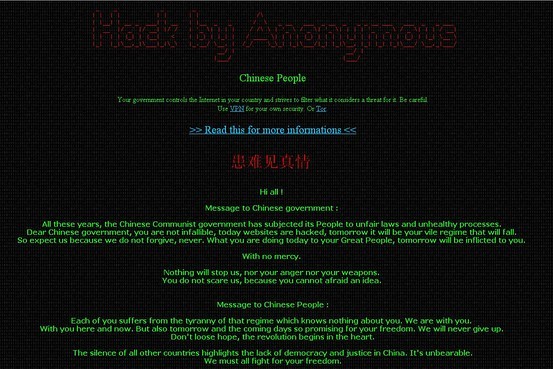
China is bolstering its security checks for state websites that do not meet standards by the end of 2015, according to top Internet regulator officials.
Cybersecurity Coordination Bureau (CCB) director Zhao Zeliang from the Cyberspace Administration of China said that the security checks for websites of the government are one of the crucial tasks of China, as the sensitive information and data are related to China's security.
"Government departments should pool more resources to speed up the security of their websites. It's also their duty to guide social websites to enhance their online security, and be their model," said Zhao during the opening ceremony of the China Cybersecurity Week that started on Monday and will run up to Nov. 30.
CCB deputy director Yang Chunyan said that the bureau already started a campaign that will verify if the "official" websites are really run by state departments.
Yang said that a unified logo will be placed on legitimate official websites so that Web users will be informed whether it is operated by government departments or not.
The unified logo will be release on Tuesday and is expected to be posted on the verified government websites in 2015, said Yang.
According to the National Computer Network Emergency Response Technical Team and Coordination Center, 2,430 state websites were hacked in the previous year, which is a 34.9 year-over-year increase.
The report said that hacking can leak sensitive information and compromise the nation's security.
In another report by Qihoo 360, the largest security application provider in China, 2,424 out of the 17,875 cybersecurity loopholes were discovered in government websites.
Qi Xiangdong, president of the security software firm, said that authorities should strengthen the security on government websites.
However, state officials are doubting whether cybersecurity products and services by enterprises are dependable or not, said Westone Information Industry chairman Li Chenggang.
Li added that the government should not depend solely on authorities with computer training and that it should utilize the technology and experience of cybersecurity giants.