Russia suspects a clever piece of malware that erases its tracks to avoid detection and can spy on computers not connected to the internet might have originated in the West but has refused to name a specific country.
The malware named "Project Sauron" is said to have been created by a group that calls itself "Strider."Both these names are characters from JRR Tolkien's Lord of the Rings trilogy.
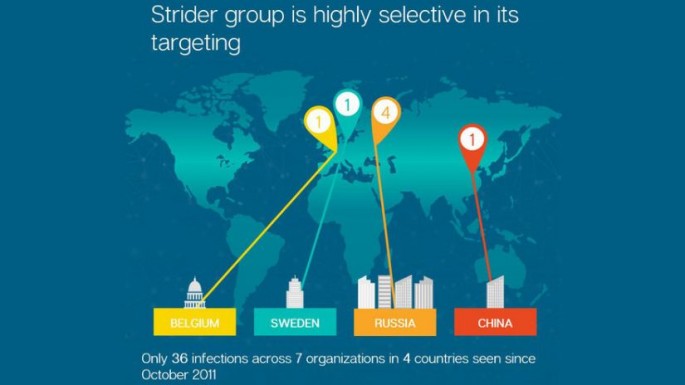
Project Sauron went undetected for five years and in that time span infected over 30 organizations in Russia, Iran and Rwanda. Many of these were government, scientific, military, telecoms and financial firms, said security research firm Kaspersky, a Russian company based in Moscow. Kaspersky Lab and American tech company Symantec Corporation both brought the malware to the attention of the public.
For its part, Symantec detected the malware in other countries, including an airline in China and an embassy in Belgium. Kaspersky first discovered Project Sauron on an unspecified "government organization" network.
"We think an operation of such complexity aimed at stealing confidential and secret information can only be executed with support from a nation state," said Kaspersky Lab.
"Kaspersky Lab has no exact data on this, but estimates that the development and operation of Project Sauron is likely to have required several specialist teams and a budget probably running into millions of dollars."
Russian media also suggests the malware might have been designed by a state-sponsored group in the West since many of the targets were in Russia and Iran.
Russia's spy agency, the Federal Security Service of the Russian Federation (FSB) reported in late July that the computer networks of some 20 Russian state, defense, scientific and other high-profile organizations were infected with malware used for cyberespionage. FSB described the operation as professionally coordinated.
It said all the cases are linked and appear to be part of a well-coordinated attack requiring considerable expertise. The coding of the malware and vectors of attack are similar to those used in previous cyber-offensive operations against targets in Russia and other nations.
"The IT assets of government offices, scientific and military organizations, defense companies and other parts of the nation's crucial infrastructure were infected," said the FSB.
FSB noted this advanced malware was tailored for each target individually based on unique characteristic of the computer under attack.
The malware monitored internet traffic, took screenshots, secretly took recordings with an infected computer's camera or microphone, logged keyboard strokes and conducted other forms of surveillance.
FSB, however, didn't reveal who it suspects is behind the cyber espionage or whether it was sponsored by a foreign government.